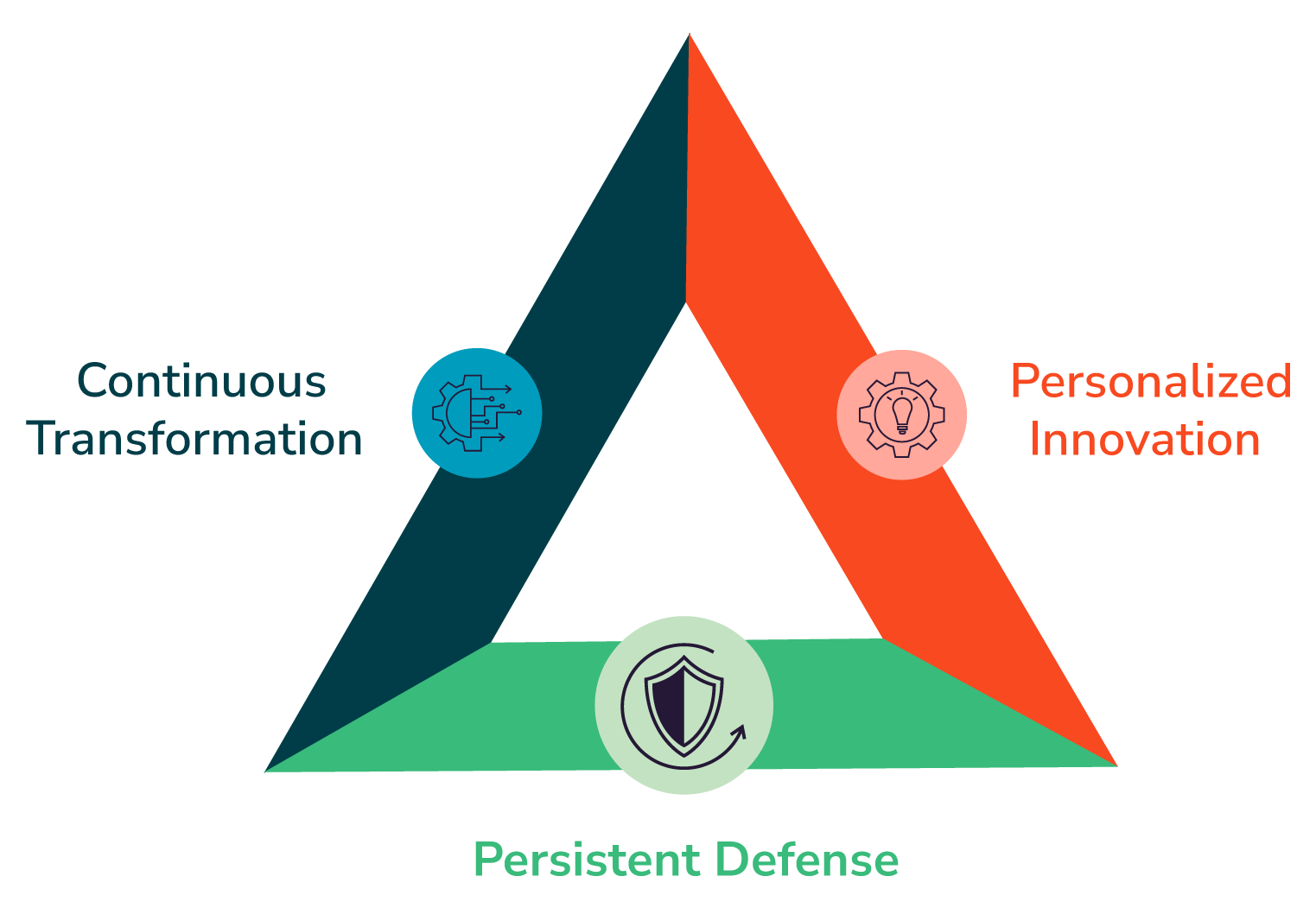
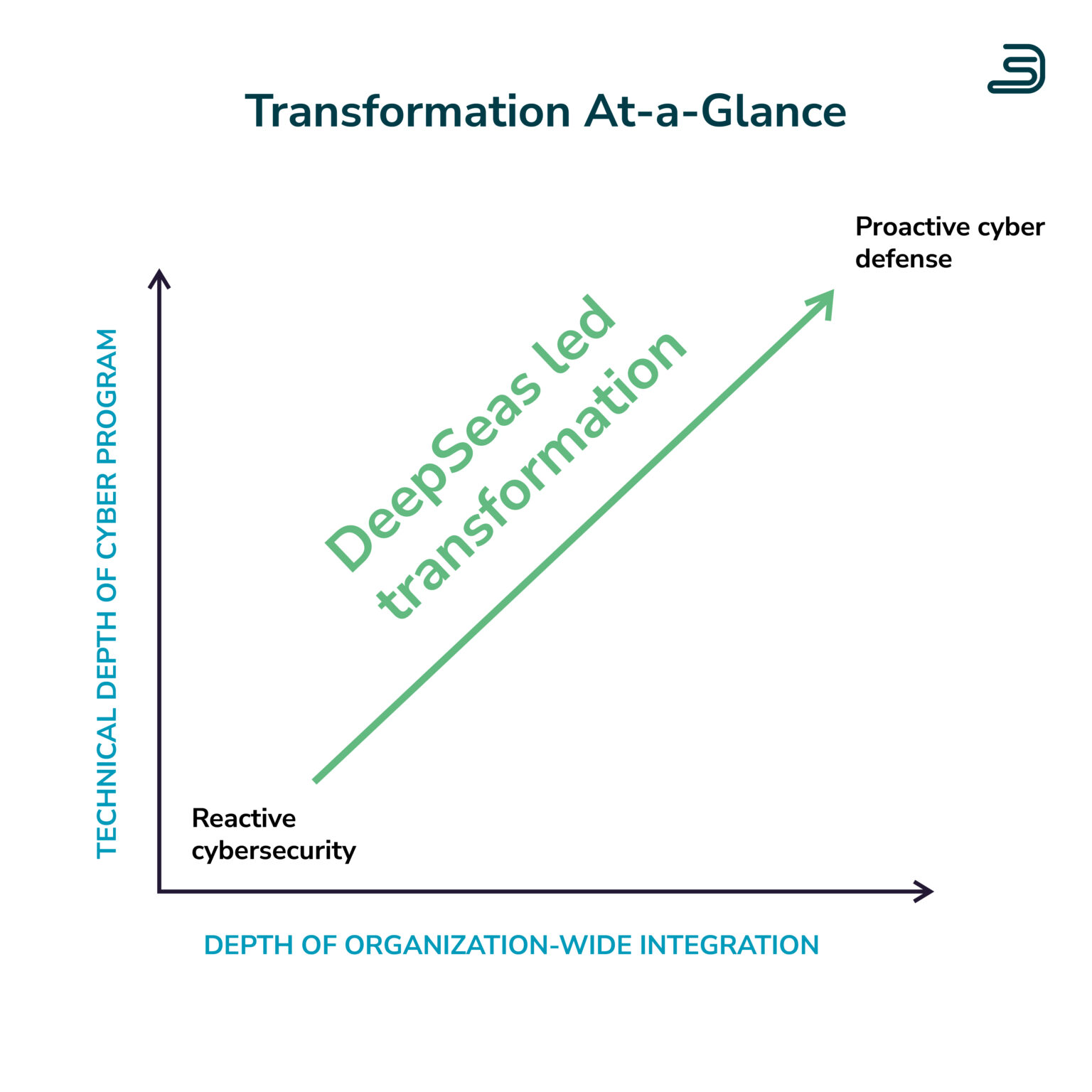
When you're ready to transform your cybersecurity program, it's OK to get help.
Craig Robinson, Research Vice President, IDC Security Services
Fuel your cyber transformation program with our flexible offerings.
Why DeepSeas?
DeepSeas is disrupting the Managed Detection & Response market with a differentiated experience for clients.
Ready to transform?
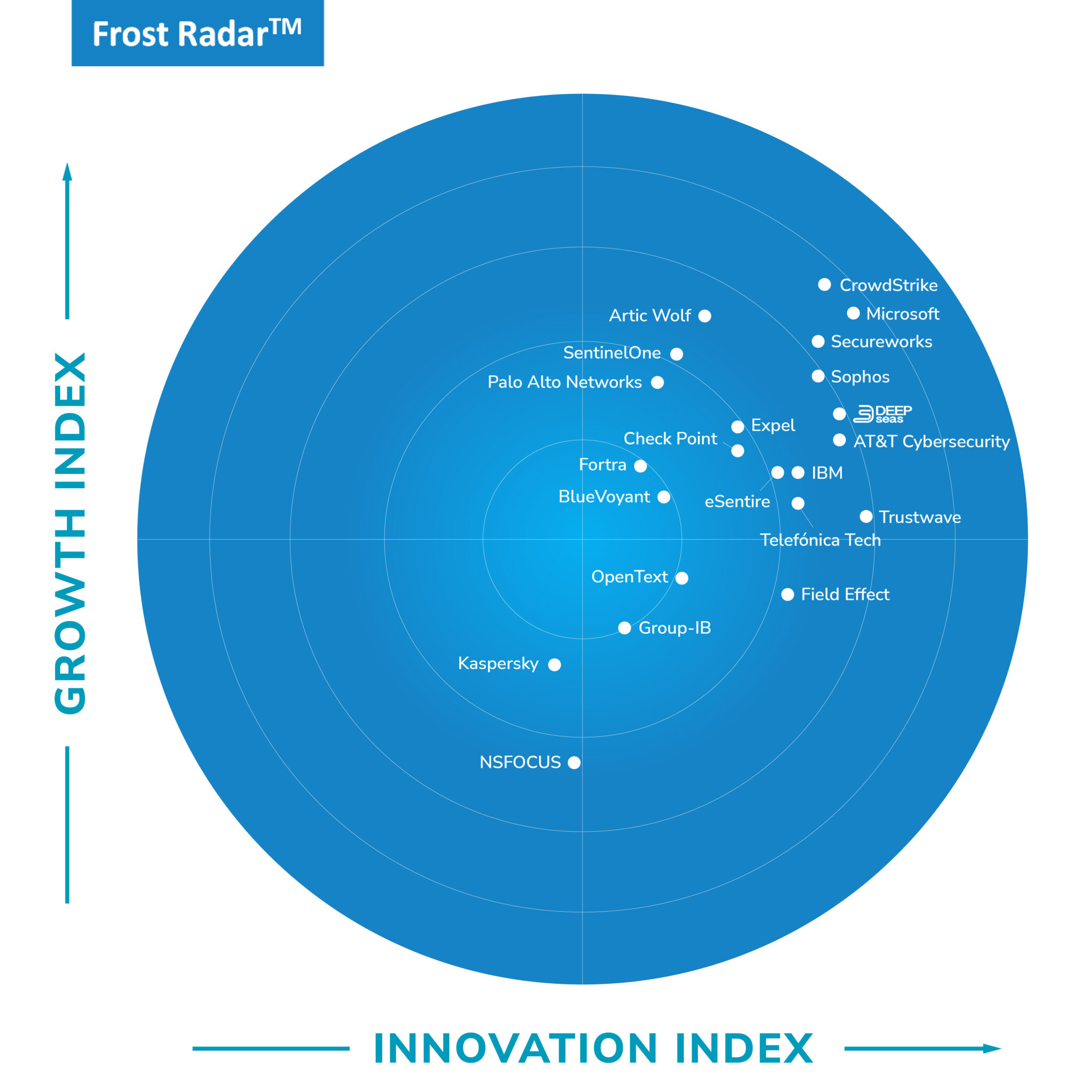
THE PROOF IS IN OUR PLATFORM.
Client Success Stories
There's one thing all
72
of our clients have in common:
They're transforming cybersecurity programs.

Manufacturer Chooses DeepSeas OT Cybersecurity Services
DeepSeas revolutionizes manufacturing cybersecurity, addressing legacy systems, real-time monitoring, and ICS threats. Our OT services seamlessly integrate with comprehensive cybersecurity solutions for enhanced protection.
Video

Pen Testing from DeepSeas RED Starts Company’s Cyber Transformation
DeepSeas RED transforms cybersecurity with long-term partnerships, not just annual reports. Our pen testing ensures meaningful change and guides clients to a safer place.
Video

Manufacturer Reduces Response Time to Cyber Threats by 90%
DeepSeas accelerates cybersecurity transformation, reducing response time to threats by 90% and phishing incidents by 77% within just 30 days. Experience rapid results today!
Video

Aerospace Company Securing Cloud Environments with DeepSeas
A client in the aerospace industry chose DeepSeas as a partner in transforming their cyber program - with a particular focus on securing cloud environments.
Video

Vulnerability Management Launched by New CISO of Broadcasting Company: Increases Visibility by 700%
A new CISO of a broadcasting company chose DeepSeas for vulnerability management as a first step to transforming the organization's cybersecurity program.
Video

Financial Institution Facing Cyber Attacks Turns to DeepSeas for Persistent Defense
Learn more about how a finance organization facing escalating cyber attacks turned to DeepSeas for a robust, multi-layered defense strategy.
Video

Life Sciences Company in M&A Process Leverages Compromise Assessment Service from DeepSeas
Learn more about how a client in the life sciences industry relied upon DeepSeas during a significant merger and acquisition process.
Video

Healthcare Company Fills Leadership Gap with DeepSeas CISO Advisory
Learn more about how a healthcare provider turned to DeepSeas CISO Advisory to resolve a significant cybersecurity leadership gap.

Multinational Pharma Company Chooses DeepSeas for Vulnerability Management & Attack Surface Reduction
DeepSeas transforms cybersecurity for a pharmaceutical giant, boosting visibility, collaboration, and defense with formalized assessments and integration of threat intelligence.
Video

Red Teaming Simulates Cyber Attack for Healthcare Organization
DeepSeas RED transforms healthcare cybersecurity, simulating real-world attacks to validate defenses, enhance processes, and ensure compliance with industry standards like NIST 800-53 and HIPAA.
Video

Manufacturer Chooses DeepSeas OT Cybersecurity Services
DeepSeas revolutionizes manufacturing cybersecurity, addressing legacy systems, real-time monitoring, and ICS threats. Our OT services seamlessly integrate with comprehensive cybersecurity solutions for enhanced protection.
Video

Pen Testing from DeepSeas RED Starts Company’s Cyber Transformation
DeepSeas RED transforms cybersecurity with long-term partnerships, not just annual reports. Our pen testing ensures meaningful change and guides clients to a safer place.
Video

Manufacturer Reduces Response Time to Cyber Threats by 90%
DeepSeas accelerates cybersecurity transformation, reducing response time to threats by 90% and phishing incidents by 77% within just 30 days. Experience rapid results today!
Video

Aerospace Company Securing Cloud Environments with DeepSeas
A client in the aerospace industry chose DeepSeas as a partner in transforming their cyber program - with a particular focus on securing cloud environments.
Video

Vulnerability Management Launched by New CISO of Broadcasting Company: Increases Visibility by 700%
A new CISO of a broadcasting company chose DeepSeas for vulnerability management as a first step to transforming the organization's cybersecurity program.
Video

Financial Institution Facing Cyber Attacks Turns to DeepSeas for Persistent Defense
Learn more about how a finance organization facing escalating cyber attacks turned to DeepSeas for a robust, multi-layered defense strategy.
Video
GET MEANINGFUL OUTCOMES FAST.
DeepSeas FAQs
At DeepSeas, we're committed to helping you understand everything involved in transforming your cybersecurity program. Below are initial FAQs to get you started.
BE THE FIRST TO KNOW.
Cyber Defense Insights from DeepSeas

DeepSeas Successfully Achieves ISO/IEC 27001 Certification
DeepSeas achieving ISO/IEC 27001 certification demonstrates its commitment to ensuring data security has been addressed, implemented, and controlled.

DeepSeas Monthly Cyber Threat Intel Rollup – December 2024
Stay ahead of cyber threats with the DeepSeas Monthly Cyber Threat Intel Rollup.

Threat Recon Unit Finds Increase in Higher Ed Cyber Threats
The DeepSeas Threat Recon Unit is seeing an increase higher ed cyber threats. In the final few months of 2024, the cybersecurity landscape grew increasingly perilous for colleges and universities. The cyber threat reconnaissance unit at DeepSeas is showing evidence that cyber criminals are refining their tactics to target institutions of higher learning, resulting in a recent surge of ransomware attacks, pre-ransomware activities, and other impactful cyber incidents that threaten operational integrity and sensitive data.
Video
DeepSeas Managed Detection & Response for Endpoint: Explainer Video
Maximize the potential of your EDR with DeepSeas Managed Detection & Response for Endpoint. Get the skilled crew and processes to help your team win.
Video

MDR-ifying Your Vulnerability Management Program
Mediocre vulnerability management programs have become the norm. Explore a revolutionary solution that redefines the approach to vulnerability management.
Video
Video

DeepSeas Monthly Cyber Threat Intel Rollup – February 2025
Stay ahead of cyber threats with the DeepSeas Monthly Cyber Threat Intel Rollup.

DeepSeas Monthly Cyber Threat Intel Rollup – January 2025
Stay ahead of cyber threats with the DeepSeas Monthly Cyber Threat Intel Rollup.

DeepSeas MDR for Endpoint
Protect devices in real-time with DeepSeas MDR for Endpoint.
Managed Detection & Response (MDR) for endpoint from DeepSeas protects your organization’s devices in real-time from malware, ransomware, and other advanced cyber threats. Utilizing 24x7 monitoring, analysis, and response, along with other advanced defensive technologies, DeepSeas will secure your endpoints – ensuring you maintain operational integrity with minimal disruption.

DeepSeas Vulnerability Management
You can't fix problems you don’t know about. Get DeepSeas Vulnerability Management.
As your organization adopts new technologies, your attack surface continues to grow and change. Knowing how to effectively identify, prioritize, and resolve risks is vital.

DeepSeas MDR for SIEM
Enrich and contextualize alerts with DeepSeas MDR for SIEM.
Managed Detection & Response (MDR) for SIEM by DeepSeas provides comprehensive security oversight by harnessing advanced analytics to identify and neutralize cyber threats, delivering 24x7, expert-driven monitoring and response tailored to your unique environment. With DeepSeas MDR, SIEM rules are deployed and fine-tuned for enhanced contextualization of machine data utilizing Endpoint Detection and Response (EDR) and Network Detection and Response (NDR) technologies. These rules enrich alerts, with SIEM use cases serving as a primary source for threat detection.

DeepSeas Successfully Achieves ISO/IEC 27001 Certification
DeepSeas achieving ISO/IEC 27001 certification demonstrates its commitment to ensuring data security has been addressed, implemented, and controlled.

DeepSeas Monthly Cyber Threat Intel Rollup – December 2024
Stay ahead of cyber threats with the DeepSeas Monthly Cyber Threat Intel Rollup.

Threat Recon Unit Finds Increase in Higher Ed Cyber Threats
The DeepSeas Threat Recon Unit is seeing an increase higher ed cyber threats. In the final few months of 2024, the cybersecurity landscape grew increasingly perilous for colleges and universities. The cyber threat reconnaissance unit at DeepSeas is showing evidence that cyber criminals are refining their tactics to target institutions of higher learning, resulting in a recent surge of ransomware attacks, pre-ransomware activities, and other impactful cyber incidents that threaten operational integrity and sensitive data.
Video

DeepSeas Managed Detection & Response for Endpoint: Explainer Video
Maximize the potential of your EDR with DeepSeas Managed Detection & Response for Endpoint. Get the skilled crew and processes to help your team win.
Video

MDR-ifying Your Vulnerability Management Program
Mediocre vulnerability management programs have become the norm. Explore a revolutionary solution that redefines the approach to vulnerability management.
Video
Join our Team
21% of the DeepSeas crew are Veterans or Active Military Reservists. Join our talented crew of cyber experts.